

Did you know August 6 is National Social Engineering Day? If you've just recently been introduced to the term social engineering, now is the perfect time to learn it, as it is one of the most common ways hackers obtain confidential information.
But don’t worry one bit. Knowledge is power! In this post, we’ll explain what social engineering is, how it works, and share tips on how to protect yourself and your business from falling victim to it.
By definition, social engineering is the power to manipulate people into sharing sensitive information. Unlike traditional hacking where technical skills are applied to breach systems, social engineering leverages the psychology in humans that leads people to share sensitive information like passwords, monetary information, or access to the system.
Social engineers often pretend to be known individuals i.e. employees, friends, or agents with authority in order to gain access to whatever they seek. They use psychological trickery, creating an illusion of urgency or trust, to get you to move quickly or innocently.
Following are the most common social engineering attacks to which you should be sensitive:
Phishing is likely the most common and dangerous form of social engineering attack. During the attack, the hacker launches a fake email, typically presenting it as though it comes from a reputable organization (for instance, your bank or a well-known company), instructing you to open a link or download an attachment. If you follow their instructions, they hack your log-in credentials, install malicious software on your computer, or access sensitive information.
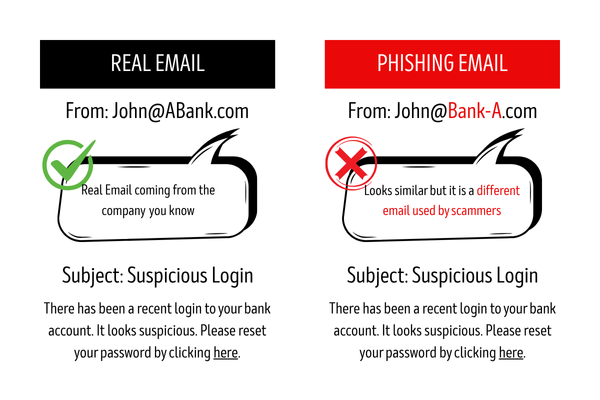
Spear phishing is way more focused than normal phishing attacks. The attacker will make the mail look like it's coming from the person you know. They could use names like your boss or your co-worker. They will usually investigate to make the message personalized, so it will be hard to detect.

Attackers use voice calls to impersonate known persons, like bank representatives or tech support, to trick you into revealing your personal information. The scammer may inform you that your account is in trouble or request a "security check."

An attacker, in pretexting, fabricates a scenario (or "pretext") to obtain personal information. They may, for example, say they are someone from your computer department calling to get your login info so that they can "repair something."

Baiting is a form of social engineering that preys on human curiosity or greed. With baiting, the hacker lures you into a trap by offering something tempting, like a free download, exclusive content, or even a USB drive labeled “confidential” left in a public place with the real goal of tricking someone into triggering a cyberattack.
If the bait is taken (ex: by plugging in a USB or installing the free software or reward, malware is activated. This can result in stolen data, complete system lockdowns, or even widespread operational damage. In fact, baiting attacks played a role in major cyber incidents in 2024.

Now that you know the types of social engineering attacks, we can proceed to how you can protect yourself and your organization from being targeted.
No matter if it's a phone call, an email, or message on social media, always verify the identity of whoever is asking for sensitive data. If they say they are your employer or bank, refrain from sharing any confidential or sentitive date with them. Instead call the institution directly using an authenticated telephone numberto verify the request.
Be cautious for:
If you have a business, make sure to educate your employees on social engineering techniques regularly. The human factor is usually the weakest link in security, so ensuring that everyone is capable of identifying a social engineering try can significantly lower the risk.
Even if a hacker manages to obtain your password, multi-factor authentication (MFA) adds an extra level of protection. It requires a second form of identification, such as a text message code or fingerprint scan, before granting access.
Make sure your devices and software are current with security patches. Cybercriminals target security vulnerabilities within outdated software to launch attacks.
Social engineering attacks are evolving very quickly, growing more complex and harder to detect. From email phishing to subtle pretexting attacks, cybercriminals are constantly finding new ways in which they can manipulate individuals and organizations into relaxing their defenses.
However, your own knowledge is your best defense. It can enable you to understand the strategies that the attackers have used and how to spot the warning signs. You can therefore reduce the danger of falling victim to these dirty tricks.
Today, on National Social Engineering Day, you have taken a moment to check how you can stay safe but don't stop here. Regularly learn about emerging threats, implement security controls, and enable additional precautions like multi-factor authentication (MFA) to stay one step ahead of cybercriminals.
Remember: Cybersecurity is an ongoing process. The more forward-thinking you are, the more effective you'll be at preventing breaches and protecting your personal and business data.
Stay informed. Stay safe. Stay one step ahead!